sudo: Authenticate with Touch ID, including Apple Watch
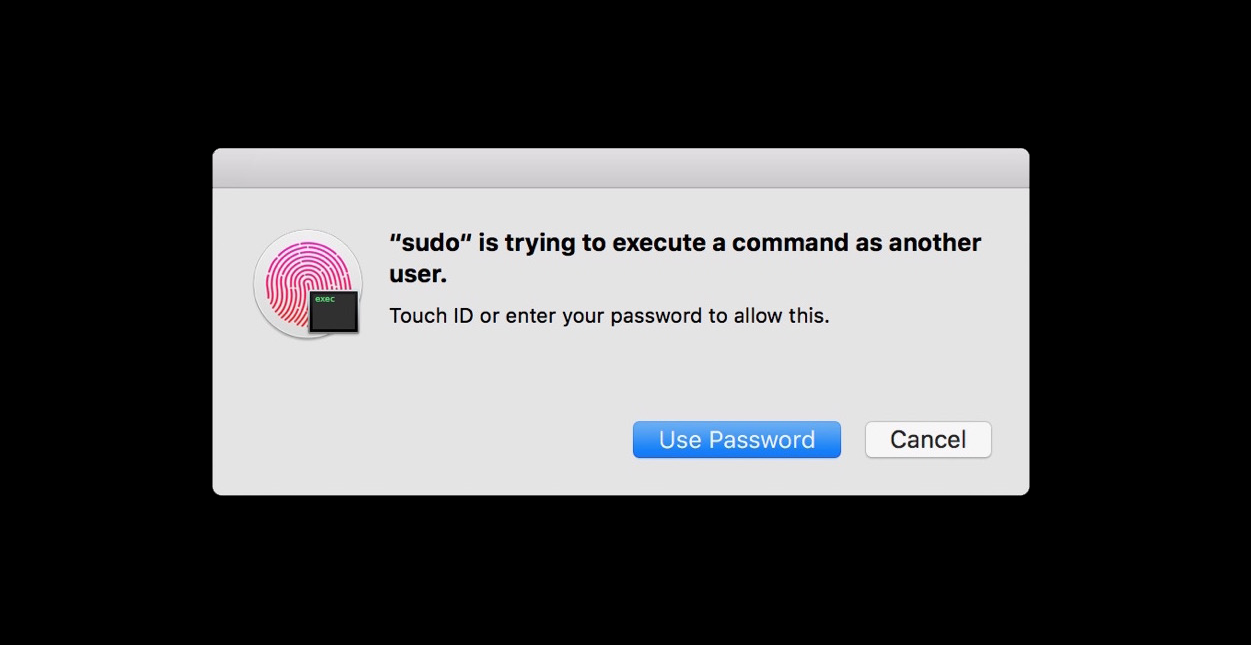
Having to enter a password when asked by a sudo command gets old, very quickly, when you have a long password. More so, it’s relatively insecure. Apart from the potential of keyboard loggers, I’m always paranoid that, however fast I can type, some hi-jinxing team mates could always be videoing my hands, fingers and keyboard! Using an external physical device, like a YubiKey for example, is much safer. However, if you have a MacBook with Touch ID or an Apple Watch, they can be used to authenticate your sudo commands instead 😎
Making an addition to the /etc/pam.d/sudo file is all that’s required.
Step 1
We need to temporarily allow the file to be modifiable, so:
| |
Step 2
Using a suitable editor (e.g. sudo vi /etc/pam.d/sudo), add the line auth sufficient pam_tid.so to the top of the file so that the contents look something like…
| |
Step 3
Important: Remember to remove those earlier permissions from the file, e.g.:
| |
That’s it
Now, when you attempt a sudo command, you’ll be prompted with a Touch ID authentication in lieu of entering your administrator password. Either respond by placing an appropriate finger on the Touch ID reader, or ‘OK’ the notification on your Apple Watch (if that’s enabled in Preferences > Security & Privacy). Yay 🎉
[UPDATE] Automating the above
Each time the OS gets updated, the modifications described above appear to get ‘reset’ to the default state (i.e. “no more sudo Touch ID for you!”). So, prompted to have to repeat these changes, I’ve wrapped them up into a script.
| |
Create a file with that content, named something like tid (for example).
Then:
make it executable
1chmod +x tidrun it
1./tid[OPTIONAL] put it somewhere in your
$PATHfor future use - choose a location that’s good for you. I noticed a location under my home directory in my$PATHthat looked appropriate.1 2# echo $PATH mv tid ~/.local/binThen it can be run at any time in future by simply issuing the command:
1tid